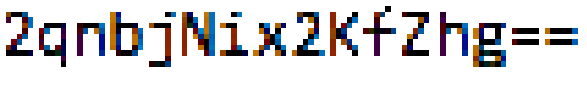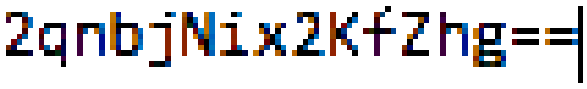This Daedalus Corp. website loads images in a rather odd way... [Source Code]
It seems like a normal page, and there appears to be nothing special within its source code. I decided to view one of the images (individually) in general in hopes of finding something there.
There's nothing special about the image itself, but the URL seemed to stick out to me the most.
http://web2014.picoctf.com/potentially-hidden-password-3878213/file_loader.php?file=zone1.jpgSpecifically that last part (
/file_loader.php?file=zone1.jpg).I decided to do a test to confirm my suspicions. I replaced '
zone1' in the link with 'zone2'. Sure enough, as soon as I hit 'Enter', the second image popped up. Now I knew that this file loader was getting the images from a directory somewhere... perhaps where the flag is too?I downloaded the Source Code given at the beginning of the problem and read through it.
Here is the PHP implemented in the source code:
<?php
$config_file = fopen("/resources/config/admin_mode.config", "r");
if (fgets($config_file) === "true") {
$flag_file = fopen("/resources/secrets/flag", "r");
echo fgets($flag_file);
flose($flag_file);
}
fclose($config_file);
?>
/resources/secrets/flagSo naturally, I pasted that text into the original link, so that it looked something akin to
http://web2014.picoctf.com/potentially-hidden-password-3878213/file_loader.php?file=resources/secrets/flagThat only led me to this page, but that doesn't mean that my efforts were unfruitful.
I've found the directory that the flag should be in! It should be located within
To account for that, I should now add
I have to add
So now that we're within the
Adding
The full link should look like:
As expected, going to that link should get you to this page:
/resources/. Since the file only looks within /resources/files, would there be a way to go up to /resources/ and into other folders rather than only look within the files folder? Yep, there is.To account for that, I should now add
../ (a directory traversal) before what I am about to type, since it, "tells the browser to move one level back toward the root directory before looking for the path to the file," (RootsWeb). Basically, it means to go up a path/folder.I have to add
../ since the flag is within /resources/, but it isn't within /resources/files/. It's within /resources/secrets/flag.So now that we're within the
/resources/ folder, we'll have to enter the /secrets/ folder and then from there get the flag from /flag. This part is relatively simple.Adding
secrets/flag after the ../ should do the trick since we'll be entering the /resources/secrets/flag folder (which is clearly where the flag file is located, according to the PHP).The full link should look like:
http://web2014.picoctf.com/potentially-hidden-password-3878213/file_loader.php?file=../secrets/flagAs expected, going to that link should get you to this page:
The only sentence (and flag) in the page is:
* Unrelated note: Potentially Hidden Password... I bet that stands for PHP, doesn't it?
i_like_being_included* Unrelated note: Potentially Hidden Password... I bet that stands for PHP, doesn't it?